DNSSEC pushing for 2048-bit RSA encryption
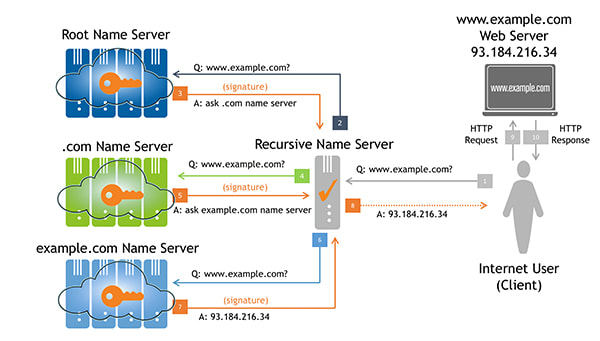
One of the most interesting and important changes to the internet’s domain name system (DNS) has been the introduction of the DNS Security Extensions (DNSSEC). These protocol extensions are designed to provide origin authentication for DNS data. In other words, when DNS data is digitally signed using DNSSEC, authenticity can be validated and any modifications detected.
A major milestone was achieved in mid-2010 when Verisign and the Internet Corporation for Assigned Names and Numbers (ICANN), in cooperation with the U.S. Department of Commerce, successfully deployed DNSSEC for the root zone. Following that point in time, it became possible for DNS resolvers and applications to validate signed DNS records using a single root zone trust anchor.
DNSSEC works by forming a chain-of-trust between the root (i.e., the aforementioned trust anchor) and a leaf node. If every node between the root and the leaf is properly signed, the leaf data is validated. However, as is generally the case with digital (and even physical) security, the chain is only as strong as its weakest link.
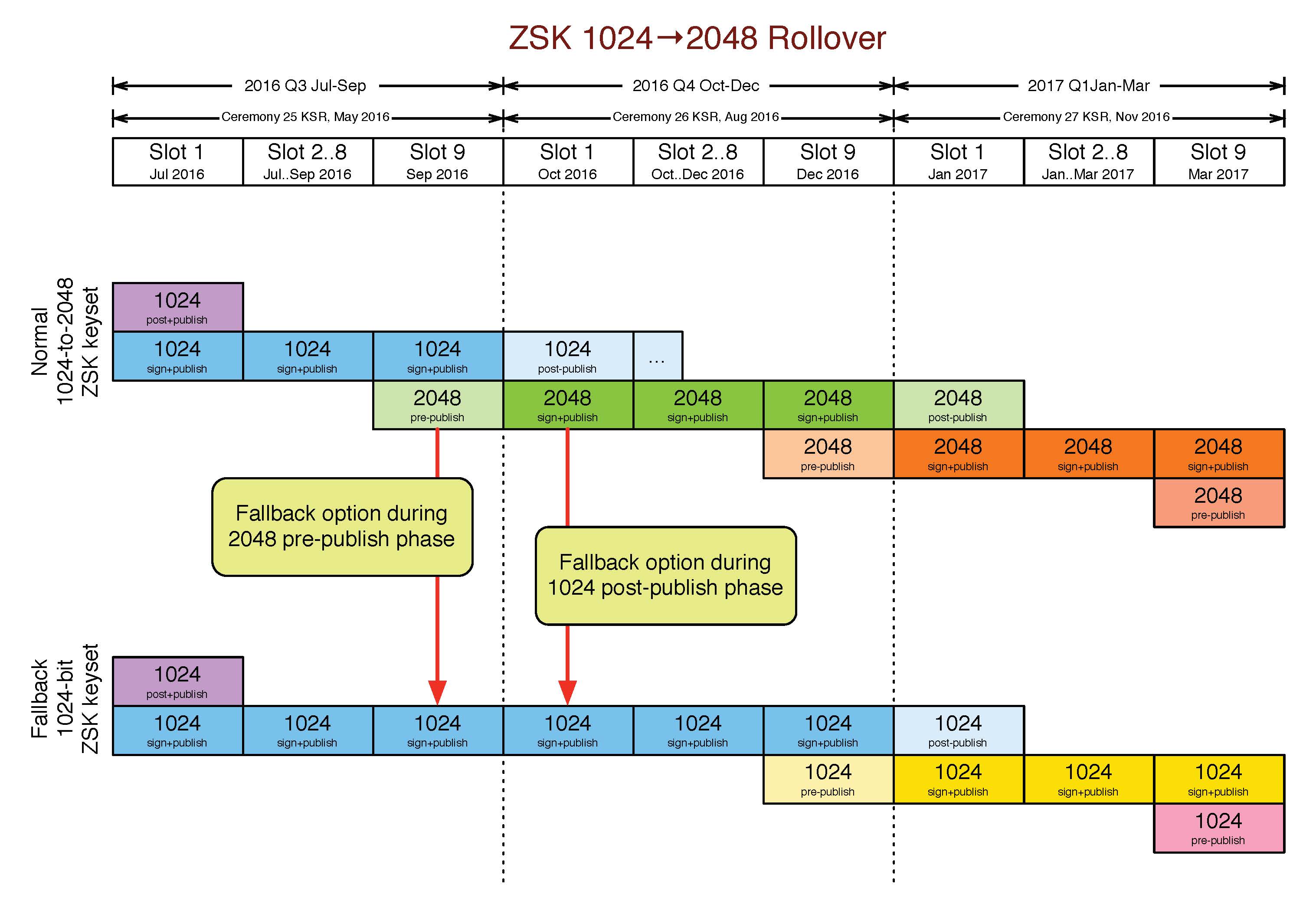
To strengthen the chain at the top of the DNS, Verisign is working to increase the strength of the root zone’s Zone Signing Key (ZSK), which is currently 1024-bit RSA, and will sign the root zone with 2048-bit RSA keys beginning Oct. 1, 2016.
Personally using 4096-bit RSA keys and flowing hashing. Not so easy to break through -- usually vigilantes are looking for easy marks with quick outcome.
You can test your network here:
http://keysizetest.verisignlabs.com/
-- web page is designed to test your network's ability to resolve domain names that have been signed with "large" DNSSEC keys
Original link:
https://blog.verisign.com/security/increasing-the-strength-of-the-zone-signing-key-for-the-root-zone/
No comments:
Post a Comment
Thank you for your comment. Will try to react as soon as possible.
Regards,
Networ King