VCDA-7wx3-G3M3-5Hkq-Gdio
VCDA-QyqN-7VvC-EWeu-127a
VCDA-kARC-hQ1q-uSLt-F8Z6
VCDA-6G1N-e6k2-5YbB-cbgT
VCDA-6yi9-N3wc-zxcZ-irQU
VCDA-Mk5W-QF4R-wmPF-QqMC
VCDA-euJ2-T1pg-s4UK-eexS
Sunday, July 26, 2020
Saturday, July 25, 2020
CEF, FIB, Routing Table
Cisco Express Forwarding separates the control plane software from the
data plane hardware, thereby achieving higher data throughput. The
control plane is responsible for building the FIB table and adjacency
tables in software. The data plane is responsible for forwarding IP
unicast traffic using hardware.
Each change in the IP routing table triggers a similar change in the FIB table. This is because the FIB table contains all next-hop addresses that are associated with all destination networks.
Cisco Express Forwarding uses special strategies to switch data packets to their destinations. It caches the information that is generated by the Layer 3 routing engine even before the router encounters any data flows. Cisco Express Forwarding caches routing information in the FIB table.
The FIB table is updated after each network change. However, it is updated only once after each network change, not multiple times, and contains all known routes.
The FIB is derived from the IP routing table and is arranged for maximum lookup throughput. The FIB table is not created from IGP and BGP databases.
Each change in the IP routing table triggers a similar change in the FIB table. This is because the FIB table contains all next-hop addresses that are associated with all destination networks.
Cisco Express Forwarding uses special strategies to switch data packets to their destinations. It caches the information that is generated by the Layer 3 routing engine even before the router encounters any data flows. Cisco Express Forwarding caches routing information in the FIB table.
The FIB table is updated after each network change. However, it is updated only once after each network change, not multiple times, and contains all known routes.
The FIB is derived from the IP routing table and is arranged for maximum lookup throughput. The FIB table is not created from IGP and BGP databases.
IPSec, GRE, DMVPN
GRE doesn't provide security, but it does provide a standardized way of
bridging the gap between two routers, making it look like there's a
dedicated local link between the routers.
GRE has multiprotocol support, including protocol 47.
GRE supports broadcast and multicast traffic, whereas IPSec only supports unicast traffic.
Routing information has to be multicast or broadcast based, and as GRE supports that, it allows routing information to be sent.
GRE can be set up as a collection of point-to-point GRE links or multipoint GRE.
GRE doesn't provide authentication services.
DES and 3DES are methods of providing IPSec confidentiality.
The Diffie-Hellman, or DH algorithms are a method of providing IPSec confidentiality through symmetric keys.
RSA is an asymmetric encryption algorithm used to provide IPSec confidentiality.
AES is a symmetric-key algorithm used to provide IPSec confidentiality.
HMAC-SHA-1 and HMAC-SHA-2 are used to provide IPSec integrity.
HMAC-MD5 is used to provide IPSec integrity.
Preshared keys and RSA signatures are used to provide IPSec authentication.
GRE has multiprotocol support, including protocol 47.
GRE supports broadcast and multicast traffic, whereas IPSec only supports unicast traffic.
Routing information has to be multicast or broadcast based, and as GRE supports that, it allows routing information to be sent.
GRE can be set up as a collection of point-to-point GRE links or multipoint GRE.
GRE doesn't provide authentication services.
DES and 3DES are methods of providing IPSec confidentiality.
The Diffie-Hellman, or DH algorithms are a method of providing IPSec confidentiality through symmetric keys.
RSA is an asymmetric encryption algorithm used to provide IPSec confidentiality.
AES is a symmetric-key algorithm used to provide IPSec confidentiality.
HMAC-SHA-1 and HMAC-SHA-2 are used to provide IPSec integrity.
HMAC-MD5 is used to provide IPSec integrity.
Preshared keys and RSA signatures are used to provide IPSec authentication.
Route Maps and Redistribution
Multiple match criteria in the same line of a route map are processed
with OR logic. Separate match criteria can also be applied vertically
under a route map line that uses AND logic. In this case, route-map
sequence 10 has multiple match statements listed vertically. Therefore,
seq 10 uses AND logic and the packet must match both ACL1 and ACL2. The
question states that the packet only matches ACL1. As a result, there is
no match and sequence 20 is checked. Sequence 20 has a single match
clause with multiple criteria. Therefore, it uses OR logic and the
packet can match ACL1 or ACL2. According to the question, it matches
ACL1; therefore, the packet is denied based on route-map sequence number
20.
For the packet to be permitted by sequence number 10, it must match all the criteria within the statement. In this case, it only matches ACL1.
Since the packet meets the criteria for sequence number 20, it will be denied by the statement and not the implicit deny any at the end of the route map.
Like access lists, route maps contain an implicit deny any as their last statement. Any packet not matching previous statements will be denied by the route map.
https://www.ciscopress.com/articles/route-maps
Question: Refer to the following partial route map:
route-map MyRouteMap permit 10
match ip address ACL1
match ip address ACL2
route-map MyRouteMap deny 20
match ip address ACL1 ACL2
Which action will be taken if a packet only matches ACL1?
Correct answer: B
It is very likely that routing loops are introduced when you use multipoint two-way redistribution. Two solutions are to redistribute only internal routes, and to use route tagging.
To avoid routing loops, either use route maps to only redistribute internal routes or use route tagging.
To avoid routing loops, either use route maps to redistribute only internal routes or use route tagging. A route tag is a 32-bit value that is attached to the redistributed routes.
Redistributing only external routes is not a way to prevent routing loops. To avoid routing loops, either use route maps to redistribute only internal routes or use route tagging. You are not able to redistribute external routes without potentially creating loops.
Redistributing internal and external routes is not a way to prevent route loops. To avoid routing loops, either use route maps to only redistribute internal routes or use route tagging. You are not able to redistribute external routes without potentially creating loops.
For the packet to be permitted by sequence number 10, it must match all the criteria within the statement. In this case, it only matches ACL1.
Since the packet meets the criteria for sequence number 20, it will be denied by the statement and not the implicit deny any at the end of the route map.
Like access lists, route maps contain an implicit deny any as their last statement. Any packet not matching previous statements will be denied by the route map.
https://www.ciscopress.com/articles/route-maps
Question: Refer to the following partial route map:
route-map MyRouteMap permit 10
match ip address ACL1
match ip address ACL2
route-map MyRouteMap deny 20
match ip address ACL1 ACL2
Which action will be taken if a packet only matches ACL1?
A. The packet will be permitted by sequence number 10.
B. The packet will be denied by sequence number 20.
C. No action will be taken.
D. The packet will be denied by the implicit deny any at the end of the route map.
Correct answer: B
It is very likely that routing loops are introduced when you use multipoint two-way redistribution. Two solutions are to redistribute only internal routes, and to use route tagging.
To avoid routing loops, either use route maps to only redistribute internal routes or use route tagging.
To avoid routing loops, either use route maps to redistribute only internal routes or use route tagging. A route tag is a 32-bit value that is attached to the redistributed routes.
Redistributing only external routes is not a way to prevent routing loops. To avoid routing loops, either use route maps to redistribute only internal routes or use route tagging. You are not able to redistribute external routes without potentially creating loops.
Redistributing internal and external routes is not a way to prevent route loops. To avoid routing loops, either use route maps to only redistribute internal routes or use route tagging. You are not able to redistribute external routes without potentially creating loops.
TCP
Question: Which option describes what happens if TCP thinks it is missing a number of data packets?
Correct answer: C
Question: IF TCP thinks it is missing a data packet, what happens?
Correct answer: C
Explanation: If TCP thinks it is missing data packet, it will half the current data rate and then slowly build it back up.
If TCP thinks it is missing data packet, it will half the current data rate and then slowly build it back up.
If TCP thinks it is missing data packet, it will half the current data rate and then slowly build it back up.
In the most basic form of reliable, connection-oriented data transfers, ignoring network congestion issues, the recipient acknowledges the receipt of each data segment to ensure the integrity of the transmission. However, if the sender must wait for an acknowledgment after sending each segment, throughput is low because it depends on the round-trip time (RTT) between sending data and receiving the acknowledgment.
Most connection-oriented, reliable protocols allow more than one segment to be outstanding at a time. This functionality can work because there is time available after the sender completes a segment transmission and before the sender processes an acknowledgment of receipt. During this interval, the sender can transmit more data as long as the window at the receiver is large enough to process more than one segment at a time. The window is the number of data segments that the sender is allowed to send without getting acknowledgment from the receiver.
Segmentation is the process TCP uses when it takes data chunks from the application layers and prepares them for shipment onto the network. Each chunk is broken up into smaller segments. Segmentation does not allow a receiving computer to advertise how much data it is able to receive before transmitting an acknowledgment to the sending computer.
SYN is a packet that TCP uses when establishing a connection between computers. The SYN packet ensures the connection is synchronized. SYN does not allow a receiving computer to advertise how much data it is able to receive before transmitting an acknowledgment to the sending computer.
TCP can receive a flow of data from application processes and then combine the data from the various processes into a single data stream through multiplexing. After TCP has multiplexed the data, it can be segmented, and then packaged and sent via the underlying Network layer protocol. Multiplexing does not allow a receiving computer to advertise how much data it is able to receive before transmitting an acknowledgment to the sending computer.
A. It updates the amount of data being sent
B. It skips the packets and requests the next logical one
C. The current TCPs wait for a timeout
Correct answer: C
Question: IF TCP thinks it is missing a data packet, what happens?
A. It updates the amount of data being sent
B. It returns received packets in sequence
C. It halves the current data rate
Correct answer: C
Explanation: If TCP thinks it is missing data packet, it will half the current data rate and then slowly build it back up.
If TCP thinks it is missing data packet, it will half the current data rate and then slowly build it back up.
If TCP thinks it is missing data packet, it will half the current data rate and then slowly build it back up.
In the most basic form of reliable, connection-oriented data transfers, ignoring network congestion issues, the recipient acknowledges the receipt of each data segment to ensure the integrity of the transmission. However, if the sender must wait for an acknowledgment after sending each segment, throughput is low because it depends on the round-trip time (RTT) between sending data and receiving the acknowledgment.
Most connection-oriented, reliable protocols allow more than one segment to be outstanding at a time. This functionality can work because there is time available after the sender completes a segment transmission and before the sender processes an acknowledgment of receipt. During this interval, the sender can transmit more data as long as the window at the receiver is large enough to process more than one segment at a time. The window is the number of data segments that the sender is allowed to send without getting acknowledgment from the receiver.
Segmentation is the process TCP uses when it takes data chunks from the application layers and prepares them for shipment onto the network. Each chunk is broken up into smaller segments. Segmentation does not allow a receiving computer to advertise how much data it is able to receive before transmitting an acknowledgment to the sending computer.
SYN is a packet that TCP uses when establishing a connection between computers. The SYN packet ensures the connection is synchronized. SYN does not allow a receiving computer to advertise how much data it is able to receive before transmitting an acknowledgment to the sending computer.
TCP can receive a flow of data from application processes and then combine the data from the various processes into a single data stream through multiplexing. After TCP has multiplexed the data, it can be segmented, and then packaged and sent via the underlying Network layer protocol. Multiplexing does not allow a receiving computer to advertise how much data it is able to receive before transmitting an acknowledgment to the sending computer.
DHCPv6
Stateless DHCPv6 works in combination with StateLess Address
AutoConfiguration (SLAAC), where an IPv6 host obtains its addressing
information from information contained within route advertisements.
However, the IPv6 host also queries a DHCPv6 server for additional
information, such as DNS or NTP server addresses. The query for other
configurations is triggered by the other-config-flag flag set in the
route advertisements. The ipv6 nd other-config-flag command is used to
configure IPv6 interface neighbor discovery to allow hosts to use a
DHCPv6 server for additional information, such as DNS or NTP server
addresses.
The managed-config-flag flag is set in route advertisements to tell IPv6 hosts to get their addressing and additional information only from the DHCPv6 server. This results in the client using the stateful DHCPv6 address assignment method, not the stateless DHCPv6 method. The ipv6 nd managed-config-flag command is used to set the managed-config-flag flag.
The ipv6 nd ns-interval command is used to configure the interval between IPv6 neighbor solicitation retransmissions on an interface. The ipv6 nd ns-interval command is not used to configure route advertisements to specify that the IPv6 DHCP client needs to use the stateless DHCPv6 address assignment method.
The ipv6 nd redirects command is used to configure neighbor redirect messages. Neighbor redirect messages are used to notify hosts of better first-hop nodes that are on the path to the destination. The ipv6 nd redirects command is not used to configure route advertisements to specify that the IPv6 DHCP client needs to use the stateless DHCPv6 address assignment method.
DHCPv6-PD is an extension to DHCPv6. Its task is to assign whole subnets from a DHCPv6 server to a DHCPv6 client. This means that, unlike classic DHCPv6 where a client receives a single address, the DHCPv6-PD client receives a set of subnets. The subnets can be segmented and dynamically applied to the client interfaces. A DHCPv6 client is usually a CPE device.
IPv6 StateLess Address AutoConfiguration (SLAAC) provides the ability to configure addressing information on host devices without any intervention from the network administrator. This configuration is achieved with the help of route advertisements that are sent by routers on the local link. Route advertisements contain one or more prefixes, prefix lifetime information, flag information, and default device information. IPv6 hosts listen for these route advertisements, takes the prefix advertised and generates the remaining 64 host bits. SLAAC does not provide the client with a set of subnets that can be segmented and dynamically applied to the client's interfaces.
When a stateful DHCPv6 server is implemented, the route advertisements need a way to tell IPv6 hosts to get their addressing and additional information only from the DHCPv6 server. This is achieved by setting the managed-config-flag flag in the route advertisements. This flag tells the hosts to disregard the prefixes in the route advertisements and query the DHCPv6 for addressing and other information. The server then allocates addresses to hosts and tracks the allocated addresses. Stateful DHCPv6 does not provide the client with a set of subnets that can be segmented and dynamically applied to the client's interfaces.
Stateless DHCPv6 works in combination with StateLess Address AutoConfiguration (SLAAC), where an IPv6 host obtains its addressing information from information contained within route advertisements. However, the IPv6 host also queries a DHCPv6 server for additional information, such as DNS or NTP server addresses. The query for other configurations is triggered by the other-config-flag flag set in the route advertisements. Because the DHCPv6 server never assigns any IPv6 addresses, it does not need to keep their state, which makes it stateless. Stateless DHCPv6 does not provide the client with a set of subnets that can be segmented and dynamically applied to the client's interfaces.
The managed-config-flag flag is set in route advertisements to tell IPv6 hosts to get their addressing and additional information only from the DHCPv6 server. This results in the client using the stateful DHCPv6 address assignment method, not the stateless DHCPv6 method. The ipv6 nd managed-config-flag command is used to set the managed-config-flag flag.
The ipv6 nd ns-interval command is used to configure the interval between IPv6 neighbor solicitation retransmissions on an interface. The ipv6 nd ns-interval command is not used to configure route advertisements to specify that the IPv6 DHCP client needs to use the stateless DHCPv6 address assignment method.
The ipv6 nd redirects command is used to configure neighbor redirect messages. Neighbor redirect messages are used to notify hosts of better first-hop nodes that are on the path to the destination. The ipv6 nd redirects command is not used to configure route advertisements to specify that the IPv6 DHCP client needs to use the stateless DHCPv6 address assignment method.
DHCPv6-PD is an extension to DHCPv6. Its task is to assign whole subnets from a DHCPv6 server to a DHCPv6 client. This means that, unlike classic DHCPv6 where a client receives a single address, the DHCPv6-PD client receives a set of subnets. The subnets can be segmented and dynamically applied to the client interfaces. A DHCPv6 client is usually a CPE device.
IPv6 StateLess Address AutoConfiguration (SLAAC) provides the ability to configure addressing information on host devices without any intervention from the network administrator. This configuration is achieved with the help of route advertisements that are sent by routers on the local link. Route advertisements contain one or more prefixes, prefix lifetime information, flag information, and default device information. IPv6 hosts listen for these route advertisements, takes the prefix advertised and generates the remaining 64 host bits. SLAAC does not provide the client with a set of subnets that can be segmented and dynamically applied to the client's interfaces.
When a stateful DHCPv6 server is implemented, the route advertisements need a way to tell IPv6 hosts to get their addressing and additional information only from the DHCPv6 server. This is achieved by setting the managed-config-flag flag in the route advertisements. This flag tells the hosts to disregard the prefixes in the route advertisements and query the DHCPv6 for addressing and other information. The server then allocates addresses to hosts and tracks the allocated addresses. Stateful DHCPv6 does not provide the client with a set of subnets that can be segmented and dynamically applied to the client's interfaces.
Stateless DHCPv6 works in combination with StateLess Address AutoConfiguration (SLAAC), where an IPv6 host obtains its addressing information from information contained within route advertisements. However, the IPv6 host also queries a DHCPv6 server for additional information, such as DNS or NTP server addresses. The query for other configurations is triggered by the other-config-flag flag set in the route advertisements. Because the DHCPv6 server never assigns any IPv6 addresses, it does not need to keep their state, which makes it stateless. Stateless DHCPv6 does not provide the client with a set of subnets that can be segmented and dynamically applied to the client's interfaces.
ESP, AH and CRC
ESP can be used by itself, or it can be used together with AH.
AH provides authentication and integrity, but not encryption.
CRC can verify data integrity, but it doesn't protect the data from being changed.
AH provides authentication and integrity, but not encryption.
CRC can verify data integrity, but it doesn't protect the data from being changed.
EVN
Easy Virtual Network (EVN) is an IP-based virtualization technology
that provides end-to-end virtualization of multiple networks. With EVN,
you can use a single IP infrastructure to provide separate virtual
networks whose traffic paths remain isolated from each other. You can
leverage the same physical infrastructure multiple times by supporting
multiple groups, each with their own logical network and unique routing
and forwarding tables.
A switched virtual circuit (SVC) is a virtual circuit that is dynamically established on demand and is torn down when transmission is complete. SVCs are used in situations where data transmission is sporadic. SVCs are not virtualization solutions that will allow you to create two separate virtual networks.
A virtual LAN (VLAN) is a group of devices on a LAN that are configured so that they can communicate as if they were attached to the same wire, when in fact they are located on a number of different LAN segments. VLANs are not virtualization solutions that will allow you to create two separate virtual networks.
A virtual private network (VPN) connects two private networks over a publicly-accessible network such as the Internet. VPNs are often used by employees working from home, employees on the road, customers, or business partners wishing to share information. VPNs are not virtualization solutions that will allow you to create two separate virtual networks.
A switched virtual circuit (SVC) is a virtual circuit that is dynamically established on demand and is torn down when transmission is complete. SVCs are used in situations where data transmission is sporadic. SVCs are not virtualization solutions that will allow you to create two separate virtual networks.
A virtual LAN (VLAN) is a group of devices on a LAN that are configured so that they can communicate as if they were attached to the same wire, when in fact they are located on a number of different LAN segments. VLANs are not virtualization solutions that will allow you to create two separate virtual networks.
A virtual private network (VPN) connects two private networks over a publicly-accessible network such as the Internet. VPNs are often used by employees working from home, employees on the road, customers, or business partners wishing to share information. VPNs are not virtualization solutions that will allow you to create two separate virtual networks.
RIPng vs RIPv2
Routing Information Protocol next generation (RIPng) is a distance
vector protocol that uses hop count as the metric. If a device has two
paths to the destination network, the path with fewer hops will be
chosen as the path to forward traffic.
RIPng operates using UDP port 521 for the transport layer protocol.
Routing Information Protocol next generation (RIPng) is enabled on an interface using the "ipv6 rip name enable interface" subcommand. If IPv6 is not enabled on the interface and you are trying to enable this same interface for RIPng, the "ipv6 rip name enable" command will be rejected.
RIPv2 sends routing updates via multicast address 224.0.0.9. RIPng uses multicast address FF02::9 to send routing updates.
RIPv2 advertises routes for IPv4 and uses IPv4 for transport. RIPng advertises routes for IPv6 and uses IPv6 for transport.
Question: Which command do you need to use to allow RIPv2 to advertise a route out of an interface from which the routing information originated?
Correct answer: C
Explanation: The split horizon feature is used to reduce the possibility of routing loops by preventing information about routes from being advertised out any interface from which the routing information originated. However, there are some network types, such as Frame Relay, that you may want the routing updates to be advertised out of an interface from which the information originated. The no ip split-horizon interface configuration command can be used to disable split horizon on the interface and allow the routes to be advertised.
Source IP addresses of incoming RIP routing updates are validated by default. The routing updates are discarded if the source address is not valid. The no validate-update-source command prevents the source IP address of incoming RIP routing updates from being validated. The no validate-update-source command is not used to allow RIPv2 to advertise a route out of an interface from which the routing information originated.
The default-information originate command is used to allow a router that is running RIP to source the default network. The default-information originate command is not used to allow RIPv2 to advertise a route out an interface that the routing information originated.
The ip summary-address rip command is used to configure the router to summarize routes that are learned via RIPv2 or that has been redistributed into RIPv2. The ip summary-address rip command is not used to allow RIPv2 to advertise a route out of an interface that the routing information originated.
RIPng operates using UDP port 521 for the transport layer protocol.
Routing Information Protocol next generation (RIPng) is enabled on an interface using the "ipv6 rip name enable interface" subcommand. If IPv6 is not enabled on the interface and you are trying to enable this same interface for RIPng, the "ipv6 rip name enable" command will be rejected.
RIPv2 sends routing updates via multicast address 224.0.0.9. RIPng uses multicast address FF02::9 to send routing updates.
RIPv2 advertises routes for IPv4 and uses IPv4 for transport. RIPng advertises routes for IPv6 and uses IPv6 for transport.
Question: Which command do you need to use to allow RIPv2 to advertise a route out of an interface from which the routing information originated?
A. ip summary-address rip
B. no validate-update-source
C. no ip split-horizon
D. default-information originate
Correct answer: C
Explanation: The split horizon feature is used to reduce the possibility of routing loops by preventing information about routes from being advertised out any interface from which the routing information originated. However, there are some network types, such as Frame Relay, that you may want the routing updates to be advertised out of an interface from which the information originated. The no ip split-horizon interface configuration command can be used to disable split horizon on the interface and allow the routes to be advertised.
Source IP addresses of incoming RIP routing updates are validated by default. The routing updates are discarded if the source address is not valid. The no validate-update-source command prevents the source IP address of incoming RIP routing updates from being validated. The no validate-update-source command is not used to allow RIPv2 to advertise a route out of an interface from which the routing information originated.
The default-information originate command is used to allow a router that is running RIP to source the default network. The default-information originate command is not used to allow RIPv2 to advertise a route out an interface that the routing information originated.
The ip summary-address rip command is used to configure the router to summarize routes that are learned via RIPv2 or that has been redistributed into RIPv2. The ip summary-address rip command is not used to allow RIPv2 to advertise a route out of an interface that the routing information originated.
IP SLA
Which of the following statements best describe Cisco IP SLAs?
A. It supports problem isolation and network planning
B. It is a contract between the provider and its customers
D. It provides a guarantee of service level
F. It specifies connectivity and performance agreements for an end-user service
NetFlow
NetFlow is used to collect traffic flow statistics from routers. This
information is helpful for performing traffic engineering and monitoring
for denial of service (DoS) attacks. The Netflow Management Information
Base (MIB) feature allows system information stored in the flow cache,
such as IP flow information, to be accessed in real time.
Syslog is the standard for logging system events. You can configure Cisco routers to forward log messages to an external syslog service. This service can reside on any number of servers, including Microsoft Windows and UNIX-based systems, or the Cisco Security MARS appliance. Syslog is the most popular message logging facility, because this facility provides long-term log storage capabilities and a central location for all router messages. Syslog logging is not used to obtain IP flow information stored in the flow cache of a Cisco router.
Certain router events can be processed by the router's SNMP agent and forwarded as SNMP traps to an external SNMP server. SNMP traps are a viable security logging facility, but require the configuration and maintenance of an SNMP system. SNMP traps are not used to obtain IP flow information stored in the flow cache of a Cisco router.
NetFlow is an accounting tool used to analyze traffic patterns in a network. NetFlow provides details about network traffic, and it can be used to capture the traffic classification or precedence associated with each flow. You can export NetFlow data to a server in which NetFlow Analyzer is running. NetFlow exports are used to export statistics from the NetFlow main cache of the router. They are not used for local retrieval of information from the cache.
Syslog is the standard for logging system events. You can configure Cisco routers to forward log messages to an external syslog service. This service can reside on any number of servers, including Microsoft Windows and UNIX-based systems, or the Cisco Security MARS appliance. Syslog is the most popular message logging facility, because this facility provides long-term log storage capabilities and a central location for all router messages. Syslog logging is not used to obtain IP flow information stored in the flow cache of a Cisco router.
Certain router events can be processed by the router's SNMP agent and forwarded as SNMP traps to an external SNMP server. SNMP traps are a viable security logging facility, but require the configuration and maintenance of an SNMP system. SNMP traps are not used to obtain IP flow information stored in the flow cache of a Cisco router.
NetFlow is an accounting tool used to analyze traffic patterns in a network. NetFlow provides details about network traffic, and it can be used to capture the traffic classification or precedence associated with each flow. You can export NetFlow data to a server in which NetFlow Analyzer is running. NetFlow exports are used to export statistics from the NetFlow main cache of the router. They are not used for local retrieval of information from the cache.
SNMP
SNMP is the most commonly used network management protocol. Currently,
Cisco IOS Software supports different security models in SNMPv1, SNMPv2,
and SNMPv3. The SNMP security level defines the cryptographic security
services that are applied to an SNMP session. SNMPv1 and SNMPv2 are not
secure protocols. The only authentication mechanisms available in SNMPv1
and SNMPv2 are community strings. Therefore, SNMPv3 should be used
whenever possible. If SNMPv3 cannot be used, you should at least use
secure SNMPv1 or SNMPv2 by using an uncommon, complex community string,
and by enabling read-only access. If community strings are also used for
SNMP traps, they must be different from community strings for the get
and set methods. This is considered best practice and it also avoids
unrelated issues in the Cisco IOS Software.
SNMP is the most commonly used network management protocol. Currently, Cisco IOS Software supports different security models in SNMPv1, SNMPv2, and SNMPv3. The SNMP security level defines the cryptographic security services that are applied to an SNMP session. SNMPv1 and SNMPv2 are not secure protocols. The only authentication mechanisms available in SNMPv1 and SNMPv2 are community strings. Therefore, SNMPv3 should be used whenever possible. If SNMPv3 cannot be used, you should at least use secure SNMPv1 or SNMPv2 by using an uncommon, complex community string, and by enabling read-only access. To configure read-only access for SNMPv1 or SNMPv2, specify the SNMP community using the snmp-server community command followed by the community string and include ro to designate the community as read-only.
SHA-1 authentication can be configured for SNMPv3 using either the authNoPriv or authPriv access modes. However, SNMPv1 and SNMPv2 do not support SHA-1 authentication.
AES encryption can be configured for SNMPv3 using the authPriv access mode. However, SNMPv1 and SNMPv2 do not support AES encryption.
SNMP is the most commonly used network management protocol. Currently, Cisco IOS Software supports different security models in SNMPv1, SNMPv2, and SNMPv3. The SNMP security level defines the cryptographic security services that are applied to an SNMP session. SNMPv1 and SNMPv2 are not secure protocols. The only authentication mechanisms available in SNMPv1 and SNMPv2 are community strings. Therefore, SNMPv3 should be used whenever possible. If SNMPv3 cannot be used, you should at least use secure SNMPv1 or SNMPv2 by using an uncommon, complex community string, and by enabling read-only access. To configure read-only access for SNMPv1 or SNMPv2, specify the SNMP community using the snmp-server community command followed by the community string and include ro to designate the community as read-only.
SHA-1 authentication can be configured for SNMPv3 using either the authNoPriv or authPriv access modes. However, SNMPv1 and SNMPv2 do not support SHA-1 authentication.
AES encryption can be configured for SNMPv3 using the authPriv access mode. However, SNMPv1 and SNMPv2 do not support AES encryption.
BGP
The "neighbor 127.0.0.1 shutdown" command is used to administratively shut down a BGP neighbor.
The "no neighbor 127.0.0.1 shutdown" command is used to administratively bring the BGP neighbor back up.
The "neighbor next-hop-self" command forces BGP to use its own IP address as the next-hop address for each network that it advertises to its IBGP neighbor, rather than letting the protocol choose the next-hop address to use.
The neighbor update-source option in the neighbor command overrides the default source IP address used for BGP packets. It is necessary to tell the router which IP address to use as the source address for all BGP packets if a loopback interface is to be used instead of the physical interface.
The "no neighbor 127.0.0.1 shutdown" command is used to administratively bring the BGP neighbor back up.
The "neighbor next-hop-self" command forces BGP to use its own IP address as the next-hop address for each network that it advertises to its IBGP neighbor, rather than letting the protocol choose the next-hop address to use.
The neighbor update-source option in the neighbor command overrides the default source IP address used for BGP packets. It is necessary to tell the router which IP address to use as the source address for all BGP packets if a loopback interface is to be used instead of the physical interface.
OSPF
The output of the show ip ospf interface command shows you all
interfaces enabled in the OSPF process.
For each enabled interface, you can see detailed information such as OSPF area ID, OSPF process ID, network type, and how the interface was included into the OSPF process.
The show ip ospf neighbor command displays OSPF neighbor information on a per-interface basis. The significant fields of the output include Neighbor ID, Priority, State, Dead Time, Address, and Interface. This command does not provide the network type being used by OSPF.
The show ip protocols command is used to show the parameters and the current state of the active routing protocol process. For OSPF, it will display information such as the OSPF router ID, number of areas in this router, and the area type. This command does not provide the network type being used by OSPF.
The show ip route ospf command gives you clearly separated lists of intra-area and inter-area routes. In addition, the output of the command gives you essential information about area border routers. This includes the router ID, IP address in the current area, the interface that advertises routes into the area, and the area ID. This command does not provide the network type being used by OSPF.
You want to choose a fast, scalable non-proprietary routing protocol for your network, what is the best choice?
For each enabled interface, you can see detailed information such as OSPF area ID, OSPF process ID, network type, and how the interface was included into the OSPF process.
The show ip ospf neighbor command displays OSPF neighbor information on a per-interface basis. The significant fields of the output include Neighbor ID, Priority, State, Dead Time, Address, and Interface. This command does not provide the network type being used by OSPF.
The show ip protocols command is used to show the parameters and the current state of the active routing protocol process. For OSPF, it will display information such as the OSPF router ID, number of areas in this router, and the area type. This command does not provide the network type being used by OSPF.
The show ip route ospf command gives you clearly separated lists of intra-area and inter-area routes. In addition, the output of the command gives you essential information about area border routers. This includes the router ID, IP address in the current area, the interface that advertises routes into the area, and the area ID. This command does not provide the network type being used by OSPF.
You want to choose a fast, scalable non-proprietary routing protocol for your network, what is the best choice?
B. OSPF
The default-information originate command is used to generate a default
external route from EIGRP into an OSPF routing domain. It is not used to configure
an EIGRP default route.
Correct. OSPFv2 uses a built-in authentication mechanism and supports plaintext and hashing with MD5 or SHA.
Incorrect. Encryption is not supported in OSPFv2. However, IPsec can be used with OSPFv3.
Correct. Simple passwords are supported but not recommended.
Incorrect. SHA is supported by OSPFv2, but the standard specie SHA-2.
Question: Refer to the exhibit. You want to ensure that traffic from R1 to Network A uses the AS path through ABR2.
Which three configurations would accomplish this task?
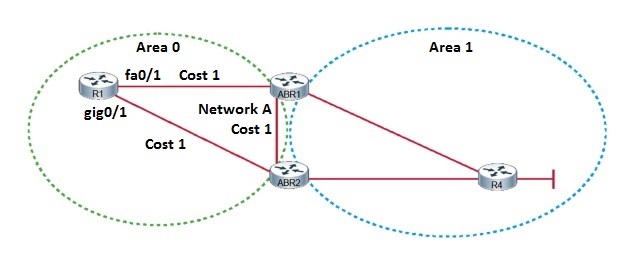
Correct answer: B C D
Your answer: B D F
Explanation: With OSPF, the paths with the lowest costs are selected as the best paths. In this case, both paths have the same cost, so the router will perform equal-cost load balancing. To ensure that traffic from R1 to Network A uses the AS path through ABR2, you need to ensure that it has the lowest cost. Cost is calculated by dividing the reference bandwidth by the interface bandwidth. The cost value is a 16-bit positive number between 1 and 65,535, and the reference bandwidth is set to 100 Mbps by default. Since Fast Ethernet and higher links have an interface bandwidth of 100 Mbps or higher, they are all assigned a cost of 1. By adjusting the reference bandwidth to a higher value using the auto-cost reference-bandwidth OSPF configuration command, the cost of the Fast Ethernet link will be higher than the Gigabit Ethernet link. The reference bandwidth value is inserted in Mbps, so a value of 1000 would assign a cost of 10 to the Fast Ethernet link, and a cost of 1 would be assigned to the Gigabit Ethernet link.
With OSPF, the paths with the lowest costs are selected as the best paths. In this case, both paths have the same cost, so the router will perform equal-cost load balancing. To ensure that traffic from R1 to Network A uses the AS path through ABR2, you need to ensure that it has the lowest cost. Cost is calculated by dividing the reference bandwidth by the interface bandwidth. The cost value is a 16-bit positive number between 1 and 65,535, and the reference bandwidth is set to 100 Mbps by default. By manually adjusting the cost for a link, you can influence the OSPF path preference. To adjust the cost of a link, you need to use the ip ospf cost interface command. In this case, adjusting the cost of the Fast Ethernet link to 10, will ensure that the Gigabit Ethernet link will be used to route traffic to Network A as it has a cost of 1.
With OSPF, the paths with the lowest costs are selected as the best paths. In this case, both paths have the same cost, so the router will perform equal-cost load balancing. To ensure that traffic from R1 to Network A uses the AS path through ABR2, you need to ensure that it has the lowest cost. Cost is calculated by dividing the reference bandwidth by the interface bandwidth. By adjusting the bandwidth of a specific interface, you can influence OSPF path preference for a specific link. To do this, you need to use the bandwidth command in interface configuration mode, which expresses a bandwidth in Kbps. In this case, adjusting the bandwidth of the Fast Ethernet link to 10,000 Kbps (10 Mbps), you change the cost of this link to 10. Since the Gigabit Ethernet link now has a lower cost, it will be used to route traffic to Network A.
Link cost is calculated by dividing the reference bandwidth by the interface bandwidth. The cost value is a 16-bit positive number between 1 and 65,535, and the reference bandwidth is set to 100 Mbps by default. Changing the reference bandwidth to 10 will not change the costs of Fast Ethernet and Gigabit Ethernet links. Both links have interface bandwidths over 10 Mbps, so they still will have costs of 1. In this case, both paths have the same cost, so the router will perform equal-cost load balancing.
With OSPF, the paths with the lowest costs are selected as the best paths. By changing the cost of the Gigabit Ethernet link to 10 Mbps, OSPF will use the Fast Ethernet link to ABR1 as it has a cost of 1.
Link cost is calculated by dividing the reference bandwidth by the interface bandwidth. The cost value is a 16-bit positive number between 1 and 65,535, and the reference bandwidth is set to 100 Mbps by default. By setting the interface bandwidth of the Gigabit Ethernet interface to 100,000 Kbps (100 Mbps), the cost of the link will remain at 1. In this case, both paths have the same cost, so the router will perform equal-cost load balancing.
You can use the "ip ospf message-digest-key" command is used to assign a key ID and key to use with neighboring OSPF MD5 routers.
You must specify if MD5 or a plaintext password is to be used.
You must use the message-digest option.
You can use ip ospf message-digest-key command to configure MD5 authentication.
Correct. OSPFv2 uses a built-in authentication mechanism and supports plaintext and hashing with MD5 or SHA.
Incorrect. Encryption is not supported in OSPFv2. However, IPsec can be used with OSPFv3.
Correct. Simple passwords are supported but not recommended.
Incorrect. SHA is supported by OSPFv2, but the standard specie SHA-2.
Question: Refer to the exhibit. You want to ensure that traffic from R1 to Network A uses the AS path through ABR2.
Which three configurations would accomplish this task?

A. R1(config)# interface gig0/1
R1(config-if)# ip ospf cost 10
R1(config-if)# ip ospf cost 10
B. R1(config)# interface fa0/0
R1(config-if)# bandwidth 10000
R1(config-if)# bandwidth 10000
C. R1(config)# router ospf 1
R1(config-router)# auto-cost reference-bandwidth 1000
R1(config-router)# auto-cost reference-bandwidth 1000
D. R1(config)# interface fa0/0
R1(config-if)# ip ospf cost 10
R1(config-if)# ip ospf cost 10
E. R1(config)# router ospf 1
R1(config-router)# auto-cost reference-bandwidth 10
R1(config-router)# auto-cost reference-bandwidth 10
F. R1(config)# interface gig0/1
R1(config-if)# bandwidth 100000
R1(config-if)# bandwidth 100000
Correct answer: B C D
Your answer: B D F
Explanation: With OSPF, the paths with the lowest costs are selected as the best paths. In this case, both paths have the same cost, so the router will perform equal-cost load balancing. To ensure that traffic from R1 to Network A uses the AS path through ABR2, you need to ensure that it has the lowest cost. Cost is calculated by dividing the reference bandwidth by the interface bandwidth. The cost value is a 16-bit positive number between 1 and 65,535, and the reference bandwidth is set to 100 Mbps by default. Since Fast Ethernet and higher links have an interface bandwidth of 100 Mbps or higher, they are all assigned a cost of 1. By adjusting the reference bandwidth to a higher value using the auto-cost reference-bandwidth OSPF configuration command, the cost of the Fast Ethernet link will be higher than the Gigabit Ethernet link. The reference bandwidth value is inserted in Mbps, so a value of 1000 would assign a cost of 10 to the Fast Ethernet link, and a cost of 1 would be assigned to the Gigabit Ethernet link.
With OSPF, the paths with the lowest costs are selected as the best paths. In this case, both paths have the same cost, so the router will perform equal-cost load balancing. To ensure that traffic from R1 to Network A uses the AS path through ABR2, you need to ensure that it has the lowest cost. Cost is calculated by dividing the reference bandwidth by the interface bandwidth. The cost value is a 16-bit positive number between 1 and 65,535, and the reference bandwidth is set to 100 Mbps by default. By manually adjusting the cost for a link, you can influence the OSPF path preference. To adjust the cost of a link, you need to use the ip ospf cost interface command. In this case, adjusting the cost of the Fast Ethernet link to 10, will ensure that the Gigabit Ethernet link will be used to route traffic to Network A as it has a cost of 1.
With OSPF, the paths with the lowest costs are selected as the best paths. In this case, both paths have the same cost, so the router will perform equal-cost load balancing. To ensure that traffic from R1 to Network A uses the AS path through ABR2, you need to ensure that it has the lowest cost. Cost is calculated by dividing the reference bandwidth by the interface bandwidth. By adjusting the bandwidth of a specific interface, you can influence OSPF path preference for a specific link. To do this, you need to use the bandwidth command in interface configuration mode, which expresses a bandwidth in Kbps. In this case, adjusting the bandwidth of the Fast Ethernet link to 10,000 Kbps (10 Mbps), you change the cost of this link to 10. Since the Gigabit Ethernet link now has a lower cost, it will be used to route traffic to Network A.
Link cost is calculated by dividing the reference bandwidth by the interface bandwidth. The cost value is a 16-bit positive number between 1 and 65,535, and the reference bandwidth is set to 100 Mbps by default. Changing the reference bandwidth to 10 will not change the costs of Fast Ethernet and Gigabit Ethernet links. Both links have interface bandwidths over 10 Mbps, so they still will have costs of 1. In this case, both paths have the same cost, so the router will perform equal-cost load balancing.
With OSPF, the paths with the lowest costs are selected as the best paths. By changing the cost of the Gigabit Ethernet link to 10 Mbps, OSPF will use the Fast Ethernet link to ABR1 as it has a cost of 1.
Link cost is calculated by dividing the reference bandwidth by the interface bandwidth. The cost value is a 16-bit positive number between 1 and 65,535, and the reference bandwidth is set to 100 Mbps by default. By setting the interface bandwidth of the Gigabit Ethernet interface to 100,000 Kbps (100 Mbps), the cost of the link will remain at 1. In this case, both paths have the same cost, so the router will perform equal-cost load balancing.
You can use the "ip ospf message-digest-key" command is used to assign a key ID and key to use with neighboring OSPF MD5 routers.
You must specify if MD5 or a plaintext password is to be used.
You must use the message-digest option.
You can use ip ospf message-digest-key command to configure MD5 authentication.
EIGRP
The Enhanced Interior Gateway Routing Protocol (EIGRP)
EIGRP supports both MD5 and SHA hashing authentication. Support for SHA was introduced in Cisco IOS 15 releases, together with the named EIGRP configuration mode.
default route can be created with the ip default-network command.
A router that is configured with this command considers the network listed in the command as the last-resort gateway and it will announce it to other routers.
The network specified by this command must be reachable by the router upon which the command is issued before it announces it as a candidate default route to other EIGRP routers.
The network specified by this command must also be passed to other EIGRP routers so that those routers can use this network as their default network and set it as the gateway of last resort. This means that either the network must be an EIGRP-derived network in the routing table or it must be generated using a static route that has been redistributed into EIGRP.
The default-information originate command is used to generate a default external route into an OSPF routing domain. It is not used to configure an EIGRP default route.
The ip route 0.0.0.0 0.0.0.0 next-hop command is used to statically configure a default route in the routing table.
This route can be used as the default route for EIGRP using the ip default-network command.
However, it must also be advertised by EIGRP using the redistribute static command.
The auto-summary command is used to turn on EIGRP automatic summarization. Automatic summarization is on by default. You can disable it using the no auto-summary command.
EIGRP can redistribute statically defined default routes by using the redistribute static configuration command. The redistribute static command redistributes all statically (manually) defined routes into the EIGRP process. Since a default route has been manually defined, this route will be redistributed into EIGRP and advertised to its neighbors.
The connected option permits the EIGRP stub router to advertise all connected routes for interfaces that are matched with an EIGRP network command. This option is enabled by default and is the most widely practiced stub option. The eigrp stub connected command can be used to enable the connected option, if it is disabled. It is not used to allow a manually configured default route to be advertised by EIGRP.
The default-information originate command can be used to generate a default external route into an OSPF routing domain. The default-information originate command, when used with RIPng, announces the default route to the neighboring routers even if there is no local default route present in the routing table. The default-information originate command is not used to allow a manually configured default route to be advertised by EIGRP.
The receive-only option restricts the stub router from sharing any of its routes with any other router within an EIGRP AS. This option does not permit any other option to be specified, because it prevents any type of route from being sent. The eigrp stub receive-only command is not used to allow a manually configured default route to be advertised by EIGRP.
Which of the following statements apply to EIGRP for IPv6 only?
EIGRP supports both MD5 and SHA hashing authentication. Support for SHA was introduced in Cisco IOS 15 releases, together with the named EIGRP configuration mode.
default route can be created with the ip default-network command.
A router that is configured with this command considers the network listed in the command as the last-resort gateway and it will announce it to other routers.
The network specified by this command must be reachable by the router upon which the command is issued before it announces it as a candidate default route to other EIGRP routers.
The network specified by this command must also be passed to other EIGRP routers so that those routers can use this network as their default network and set it as the gateway of last resort. This means that either the network must be an EIGRP-derived network in the routing table or it must be generated using a static route that has been redistributed into EIGRP.
The default-information originate command is used to generate a default external route into an OSPF routing domain. It is not used to configure an EIGRP default route.
The ip route 0.0.0.0 0.0.0.0 next-hop command is used to statically configure a default route in the routing table.
This route can be used as the default route for EIGRP using the ip default-network command.
However, it must also be advertised by EIGRP using the redistribute static command.
The auto-summary command is used to turn on EIGRP automatic summarization. Automatic summarization is on by default. You can disable it using the no auto-summary command.
EIGRP can redistribute statically defined default routes by using the redistribute static configuration command. The redistribute static command redistributes all statically (manually) defined routes into the EIGRP process. Since a default route has been manually defined, this route will be redistributed into EIGRP and advertised to its neighbors.
The connected option permits the EIGRP stub router to advertise all connected routes for interfaces that are matched with an EIGRP network command. This option is enabled by default and is the most widely practiced stub option. The eigrp stub connected command can be used to enable the connected option, if it is disabled. It is not used to allow a manually configured default route to be advertised by EIGRP.
The default-information originate command can be used to generate a default external route into an OSPF routing domain. The default-information originate command, when used with RIPng, announces the default route to the neighboring routers even if there is no local default route present in the routing table. The default-information originate command is not used to allow a manually configured default route to be advertised by EIGRP.
The receive-only option restricts the stub router from sharing any of its routes with any other router within an EIGRP AS. This option does not permit any other option to be specified, because it prevents any type of route from being sent. The eigrp stub receive-only command is not used to allow a manually configured default route to be advertised by EIGRP.
Which of the following statements apply to EIGRP for IPv6 only?
B. Uses Multicast
C. Automatic summarization is not possible
Which two of the following are used in EIGRP metric calculations by default? (Choose two)
Subscribe to:
Posts (Atom)